To gain insight into the state of development, every year tens of thousands of developers are surveyed by Stack Overflow through their service. Stack Overflow serves as a stage where designers share their work and make inquiries identified with coding. Consistently, the site overviews a huge number of engineers to get a thought regarding the present situation of the tech world, making it a standout amongst the most exhaustive designer study ever directed.
Every year the statistics of inside industry are fascinating and this year for 2016’s study, 50,000 to 56033 developers responded from across the industry from 173 countries– and the findings are fascinating, as well as insightful. The company found that JavaScript is still overwhelmingly the most popular development language, with more than 55.4 percent of people saying they use the language. PHP fell 4 percent in the last year to 25 percent, which Stack Overflow attributed to the rise of Node and Angular, but Microsoft’s Visual Basic is the most “dreaded” language. It was also found that 46 percent of the developers have no degree in computer science or any related field and that more than 57 percent of them check in code at work more than once a day.
Survey statistics of January 2016 showed, more than 45 million opened Stack Overflow in their web programs to pose a question or answer something asked by a kindred designer. Most respondents recognize themselves as full-stack designers with a number as high as 28%, trailed by back-end web engineers with 12.2%.
Among overall participants, the most popular developer job title was “Full-Stack Web Developer” at 28 percent, followed by “back-end developer” at 12 percent and around 11.4% percent call themselves an understudy, trailed by 8.4% developers who are Android, iOS, Windows Phone, and multi-stage development developers. Interestingly the most common developer age is 25-29, with more than 28 percent of respondents fitting into the category, followed by 23 percent at 20-25.
Stack overflow engineer overview 2016 designer occupations: 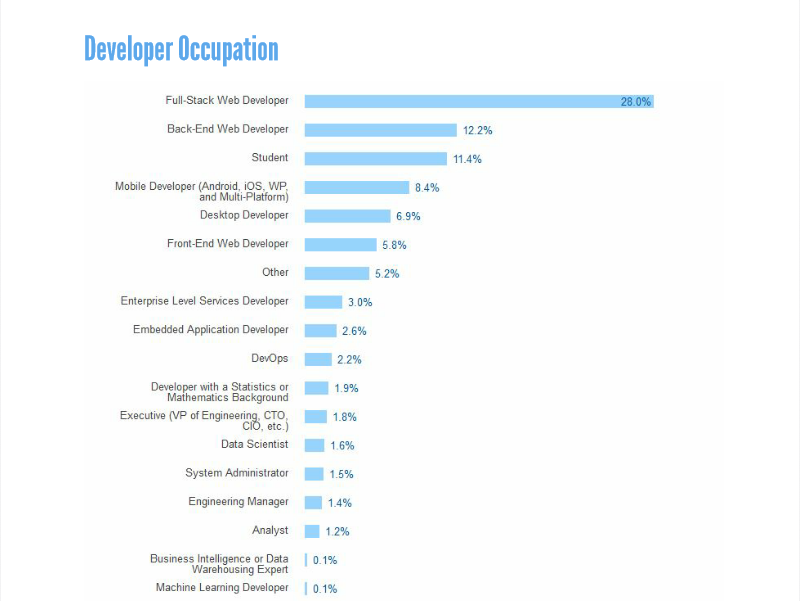
If we move to the area where we’ll discuss the most utilized advances, JavaScript keeps on decision the web. It’s still the most mainstream programming dialect for web advancement with 55.4% individuals saying that they code in JavaScript. This colossally famous programming dialect is trailed by SQL Server (49.1%), Java (36.3%), C# (30.9%), PHP (25.9%), and C++ (19.4%).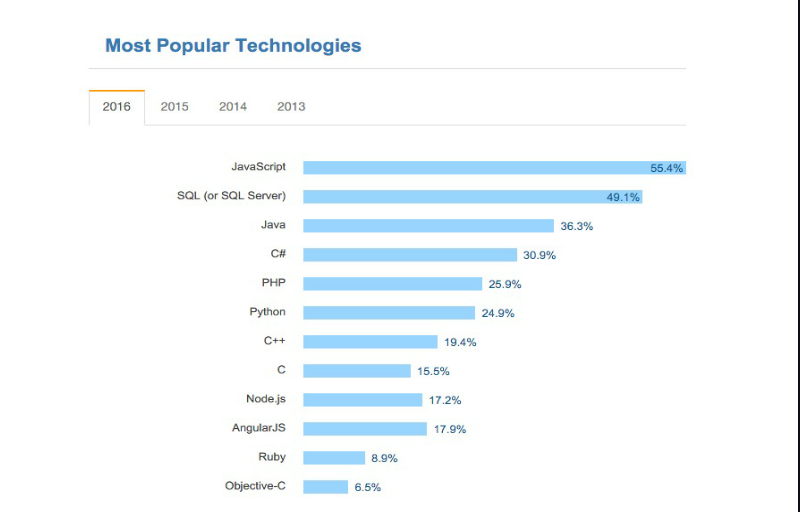
In “Stack Overflow engineer review 2016 most prevalent technologies”, if we discuss the inclining advancements on Stack Overflow, React, Spark and Swift (taking business sector from Objective-C ‘quickly’) are administering the graphs, while Node.js and Angular JS are on the rise.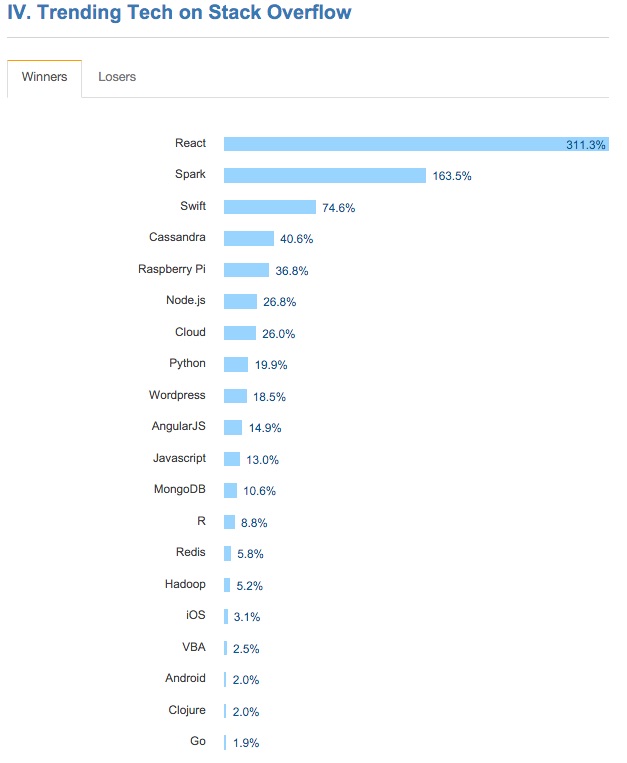
This year we asked respondents if they are Engineers, Experts, Hackers or any of the other descriptors we’ve frequently seen in job listings, business cards, and Twitter bios.
95% of developers identify as either a Developer, Programmer, Engineer, Senior Developer or Full-Stack Developer. Embedded Application Developers are most likely to identify as Engineers. Graphics Programmers are most likely to identify as Programmers.
But Developer is the runaway choice in this survey.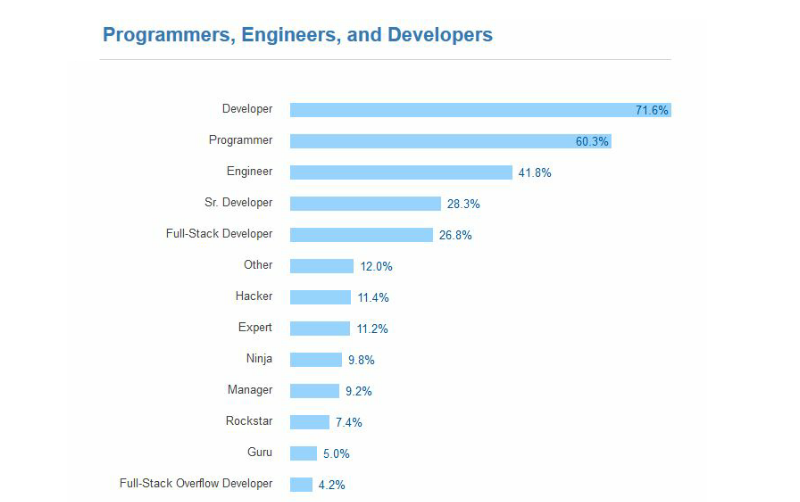
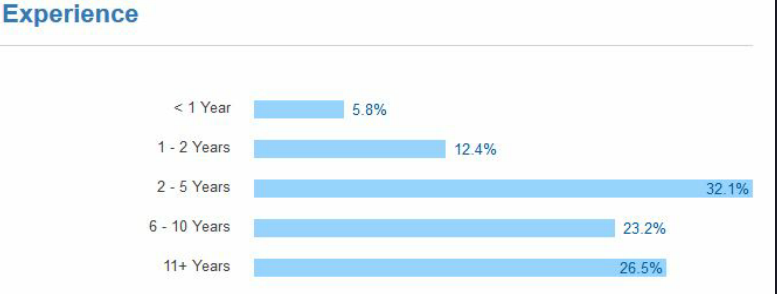
The average developer has about 6.5 years of IT or programming experience. This isn’t necessarily professional experience (the average student tells us they have 3.4 years of experience). Developers gain experience by building things, even if they’re doing it unpaid or part-time. We’ve found this experience distribution to closely match that of more than 230,000 developers who make their CVs available on Stack Overflow.
Worldwide, the median Front-End Web Developer has 3.5 years of experience. The median Full-Stack Developer has 8 years of experience. And the median Engineering Manager has 13 years of experience.
The other points that were highlighted in Survey were, 69% of all developers tell us they are at least partly self-taught. (13% of respondents across the globe tell us they are only self-taught.) 43% of developers have either a BA or BS in computer science or a related field. 2% of developers have a PhD.
Overall, about 73% of developers tell us they think diversity is at least somewhat important in the workplace. 41% of developers say diversity is very important. And developers who most often influence hiring decisions are more likely to believe in the value of diversity than other developer types.
The saddest statistic in the Survey document, which has been highlighted as a major issue at many silicon valley tech companies, is that more than 92 percent of the respondents were male, showing just how gendered the industry really is and how far we need to go.
The study provides a lot of other interesting data if you’re looking for insights into where to move next, or if you’re looking for an easy pay bump. Mantra Labs has been continuously keeping watch on latest trends in Tech companies, to know more about latest trends, connect to Mantra Labs.
Knowledge thats worth delivered in your inbox