The Mobile World Congress is the largest mobile trade fair, which wrapped up in Barcelona on Thursday. The conference recorded 2199 exhibitors and attendance of over 101000 people, which was covered by 3,600 members of the international press and media.
This year the conference was dominated by the arrival of advanced technology like wearable technology, robotics, advanced mobiles, virtual reality, smart machines, ultra-fast 5G networks, INVISIBLE CHARGERS, connected objects, HOLOGRAMS, LiFi evolution and development of other advanced gadgets. MWC was more focused on the future trends in technology and the business impact of mobility and other tech gadgets. Many announcements were made and many technologies were showcased which gave goosebumps.
Here are some of the launches and future technology announcements that were made in MWC 2016 which caught attention of the visitors, business-hubs and media:
Wearable
Tying in with the internet of things is wearable tech, it is expected to be a big deal. Plenty of activity trackers, sleep monitors and other devices were showcased, which keep track of your health and wellbeing.
The focus was around the activity around the wearable pavilion, with everything from smart watches and glasses to smart fabrics demonstrated.
Michael O’Hara of the GSMA points out that we are embedding mobile in everything in our lives – which makes the show the perfect place to showcase the latest mobile developments.
This opens up new opportunities for vendors, app developers, and accessory makers. The smartphone will become the hub of a personal-area network consisting of wearable gadgets. These gadgets will communicate with mobile applications to deliver information in new ways and enable a wide range of products and services in areas such as sport, fitness, fashion, hobbies and healthcare. Thus, wearable devices connected with smartphones will influence the next generation of mobile application development strategies.
Virtual Reality
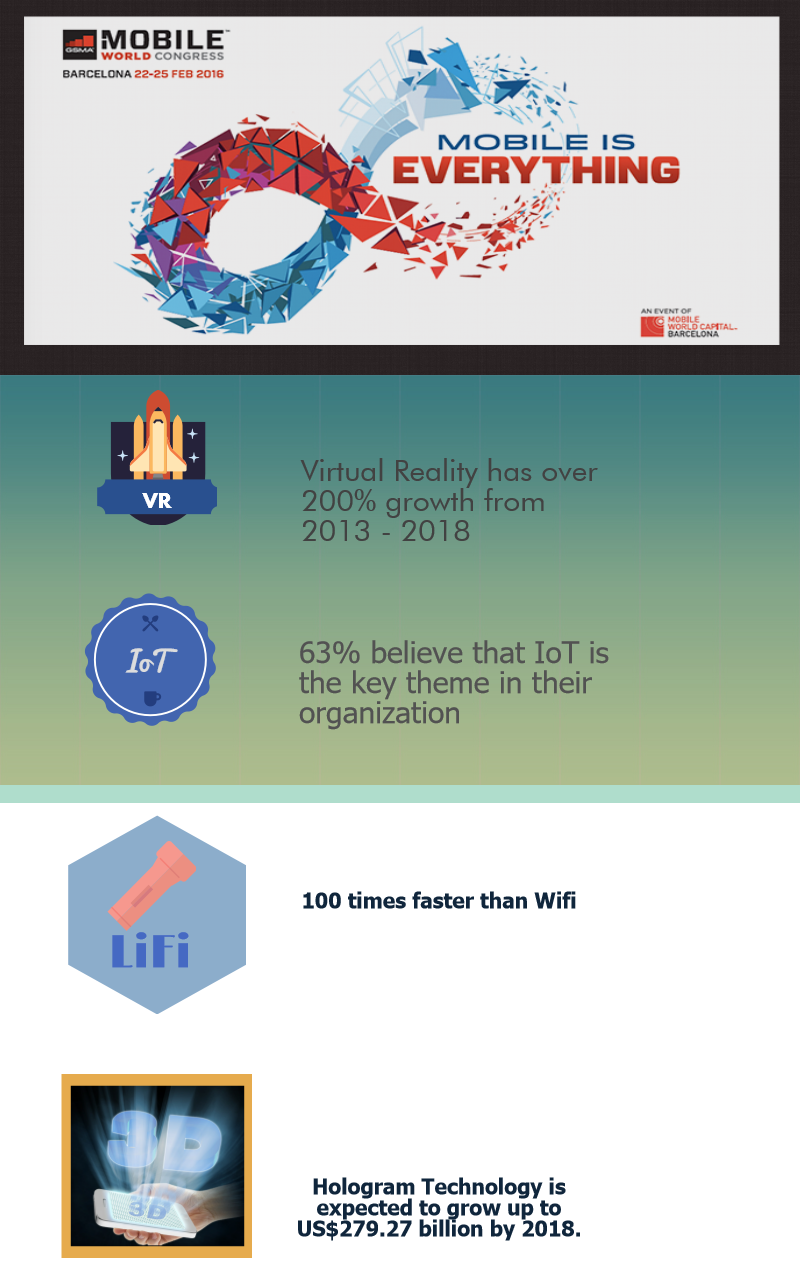
Virtual reality was featured heavily at the show. With the speech and support by Mark Zuckerberg and a showcase of VR sets on the stage of the Samsung Galaxy, it grabbed spotlight in conference.
The headsets for the Galaxy line of smartphones is partly powered by Oculus, which is owned by Facebook, and is a good gateway product to the more advanced Oculus Rift that goes on sale in the next couple of months. The conference proved good chance to showcase the latest updates on VR, as the device had some tweaks when initially previewed.
Lots of other wearable headsets were also showcased which are designed to press your mobile phone into service as a screen, making it a more budget-friendly way to get into VR. HTC and Sony also unveiled its PlayStation VR. Google also announced their work on a new headset to work with smartphones.
The emphasis on smartphone VR is going to be the next big thing, given that most of the ingredients to turn your phone into a virtual reality wonderland are already there. Everything will change a thousand times before it ever settles. VR device will attach unnoticed to the frame of your glasses, which would be connected through mobile apps; maybe it’ll be powered entirely by a button on your shirt or your brain waves, which would be connected by Application. We’ll use VR for everything from simple games and movies to robotic surgery and wildly futuristic military applications, which would be operated by Applications. We’re building better apps for future to connect with VR sets.
Internet of Things
Mobile technology is a large part of making the internet of things a more welcome prospect for consumers. Connected devices would soon infiltrate everything from your home to your car, allowing them to communicate through more open platforms than before.
“Smartphones have become a sort of black hole integrating a huge array of sensors, but mobile is now exploding back out to our environments.
“Sensors and connectivity are expanding beyond smartphones, on our wrists, bodies, cars, TVs, washing machines, but also in invisible places in buildings and the world around us,” Forrester’s Thomas Husson wrote.
While there were lots of discussions and speeches about mobile simply being a subset and key to unlock IoT revolution.
The future of mobile app development isn’t simply about our mobile phones and tablets anymore. The Internet of Things will be even bigger in the near future, even though current efforts are being made to make IoT better. Smart objects will be a part of the Internet of Things and will communicate through an App on a smartphone or tablet. Smartphones and tablets will act as remote controls, displaying and analyzing information, interfacing with social networks to monitor “things” that can tweet or post, paying for subscription services, ordering replacement consumables and updating object firmware.
As devices start to get even more interconnected, the opportunity for software developers, to add value to these smart devices will become ever greater. Eventually, the competition between these devices will be mostly based on which has the best quality software. This is where the future of mobile app development becomes an ocean of opportunity for mobile app developers.
 LiFi evolution
LiFi evolution
Speculation, Apple may deploy Lifi support in future iOS devices continues, and MWC saw pureLiFi launch its LiFi-X dongle, an access point that connects to any LED light to help create a LiFi network. Harald Haas, CEO of pureLiFi, said: “It’s exciting that so many of the tech giants are now engaging directly with LiFi through pureLiFi technologies… We have witnessed rumours that Apple is investigating ‘LiFi-Capabilities’ in their latest iOS 9.0,” he added, “We now have a rail-track technology for the lighting industry to develop exciting and new business models around light as a service (LaaS).”
With the advent of LIFI, the limitations associated with slow networks will be a thing of the past. Mobile App architectures will have to scale up with better server specifications and more optimized code on the front-end to ensure that they don’t become limitations in the performance factor of mobile apps.
Holograms Make An Appearance:
Which science fiction fan has not dreamed of being able to speak to someone far away by hologram? Several firms believe this will be possible when faster 5G mobile networks are running.
Among them is US start-up Leia Inc, named after the heroine of the “Star Wars” franchise, which presented a system that creates a 3D image that appears to float above the screen of a tablet.
SK Telecom’s stand featured a beam of green light which caused different images to appear inside it such as a dolphin, a heart or a gymnast’s movement.
The Hologram technology is in its nascent stage currently, but it has plenty of rooms to prosper in the future. It runs on a software that relies on ultrasonic waves. With the advent of mobile apps, the Hologram technology is going to make communication easier and intuitive.
In short, MWC represented all horizontal and vertical sectors of the mobile industry, which would be future of new-age technology.
Knowledge thats worth delivered in your inbox





