The insurance industry has been thriving to establish a strong connection with customers. The challenge is, however, intense with digital disruption and new avenues for customer risks. Insurance companies are catching the pace of the technological revolution and harnessing technology to bring more relevant products to the customers. While ‘customer satisfaction’ lies at the centre of businesses today, is insurance moving up the customer experience value chain? Let’s see.
Insurance Now and a Decade Ago
Traditionally, a customer would call the insurance company during instances of claims. The customer would hear from the company only when the policy renewal time is approaching. This indicates the need for an ice-breaker in the insurance-customer relationship.
A decade ago, insurers intended to harmonize customer interactions — the touchpoints. Normally, any insurance company can have 4-7 customer touchpoints. Even though individual touchpoints are performing, the overall experience for a customer might not be satisfactory.
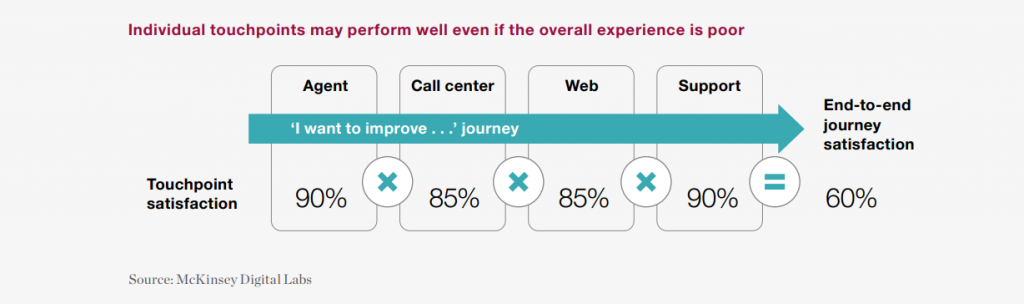
Customer satisfaction depends on five factors: interaction; price; policy offerings; billing & payment; and claims. However, to train the entire organization to see the interactions with customers’ eyes is still a challenge. It’s not possible to revamp the entire system overnight, but identifying the pain-points and acting upon them can surely move insurers up the ‘experience’ value chain.
For instance, the year 2014-15 witnessed one of the hefty market slowdowns in the automobile sector. Despite this, the millennials expressed an increase in satisfaction for their car-insurance services. The main reason for the increased satisfaction in the customer experience value chain was measurably improved interactions.
Resource: “Improved Interactions Drive Gen Y Increase in Auto Insurance Satisfaction.”
Addressing the fact that more touchpoints lead to more operational challenges and time to deliver results; insurers prototyped single-point-of-contact models during 2015-16. Here, a personalized agent would take care of the customer interactions. The results were profound, and this step is a milestone in defining the customer journey as a whole. McKinsey’s research finds that customer journeys are more strongly correlated with business outcomes than touchpoints.
Also read: Customer Journey is the New Product!
Today, organizations are leveraging technologies to speed-up processes like policy distribution, underwriting, and claim settlements. For instance, USAA (The United Services Automobile Association) is developing machine learning models to instantly predict vehicle damage from digital images and offer claim estimates.
Recent Developments in Insurance
According to Accenture, 76% of customers would switch providers for more personalized service and tailored product offerings. Insurers are, therefore, not only concerned about “what my customers want,” but also – “how my customers want.”
Organizations are using technology to provide tailored solutions to customers specific to their requirements. Artificial intelligence (AI), Machine Learning (ML), IoT, Blockchain, and Data analytics are strengthening the insurtech sector.
Carriers are using AI and ML to improve underwriting for mitigating risks. For example, Cape Analytics uses AI and geospatial imagery to provide instant property intelligence. Insurers can, therefore, accurately assess a property’s risk and value.
As mentioned before, claim settlement is one of the five major factors influencing customer satisfaction in insurance. Insurers are leveraging AI and cloud technology to settle claims in minutes or even less. For example, ICICI Lombard uses Cognitive Computing, Intelligent Character Recognition (ICR), and Optical Character Recognition (OCR) to automate the claim settlement process. Similarly for health insurance, ICICI Lombard is covering medical procedures like Cataract, Maternity, Appendicitis, Hemodialysis, and Hysterectomy for app-based claim settlement.
Also read – how AI can settle claims in 5 minutes!
Insurance companies are also automating workflows inline with their existing processes. It is helping insurers to bridge the technology gap between Gen X, Millennials, and Gen Z customers. Efficient insurance workflow automation solutions are trained to decipher industry-specific jargon and at the same time, interact with the user using NLP (Natural Language Processing) techniques.
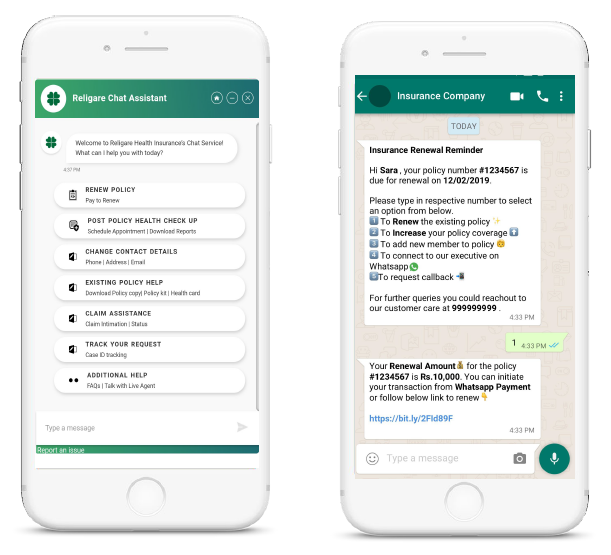
Another remarkable advancement in insurance CRM is the adoption of chatbots. It is a viable solution to serve multiple customers concurrently. For example, Religare, a leading insurer was able to increase customer interactions by 10x through chatbots.
The present time also sees customers’ growing intent towards micro policies, which serve a single purpose instead of an all-encompassing insurance scheme. Technology is also helping to distribute micro policies in scale with almost zero upfront costs. For example, Gramcover, an Indian microinsurance startup uses direct-document uploading and processing for distributing policies in rural areas.
What Customers Say?
The World InsurTech Report 2019 indicates that less than 25% of business customers and 15% retail policyholders believe they’re covered against all emerging risks. However, 28% of individual customers are amenable to share additional data for more comprehensive services. Also, 15% of customers are willing to pay an additional fee for relevant services.
The takeaway — ‘relevance’ is the key to today’s customers. Insurance companies can leverage this opportunity to provide products related to emerging threats like identity theft, privacy invasion, misuse of personal information, and attacks from ransomware.
In 2018, about 30% of customers selected their insurer in a single day, according to a survey from the Insurance Information Institute. Through creating exceptional customer experiences, insurers can set themselves apart from their competitors. And the answer to ‘how’ to create this exceptional experience lies in focusing on the journey more than the customer touchpoints.
The customer interaction preferences will keep on changing. Today, millennials prefer to interact with insurers via digital self-service. Tomorrow, Gen Z might want complete automation, i.e. no interaction at all. How fast the insurance industry adapts to the changing preferences will determine the level of satisfaction in the customer experience value chain.
We provide insurtech solutions for business-specific challenges. Feel free to drop us a line at hello@mantralabsglobal.com, illustrating your requirements.
Knowledge thats worth delivered in your inbox





